IPBan Pro, when running on Windows, uses a low level Microsoft technology called Windows Filtering Platform.
This provides significant performance improvements compared to Windows firewall, which most people are familiar with. The only downside is that low level Windows Filtering Platform rules do not show in Windows Firewall. To get around this, IPBan Pro provides three ways to view the low level rules created in Windows Filtering Platform.
1. You can query Windows Filtering Platform from an admin powershell:
netsh wfp show filters "file=c:/filters.xml"; notepad "c:/filters.xml"
This will then open the filters.xml in notepad where you can search for IPBan_ and find rules that IPBan Pro has created.
As of version 2.5.0, firewalld is used for Linux and you can view rules in the public zone at /etc/firewalld/zones/public.xml. Sets are in /etc/firewalld/ipsets.
On Linux versions older than 2.5.0, iptables is used and the various iptables Linux tools can be used to view ip addresses, such as ipset -L and iptables -L.
2. As of version 2.4.0, in the machines tab, right click on the FQDN of the machine to view firewall rules for and select the option to view firewall rules.
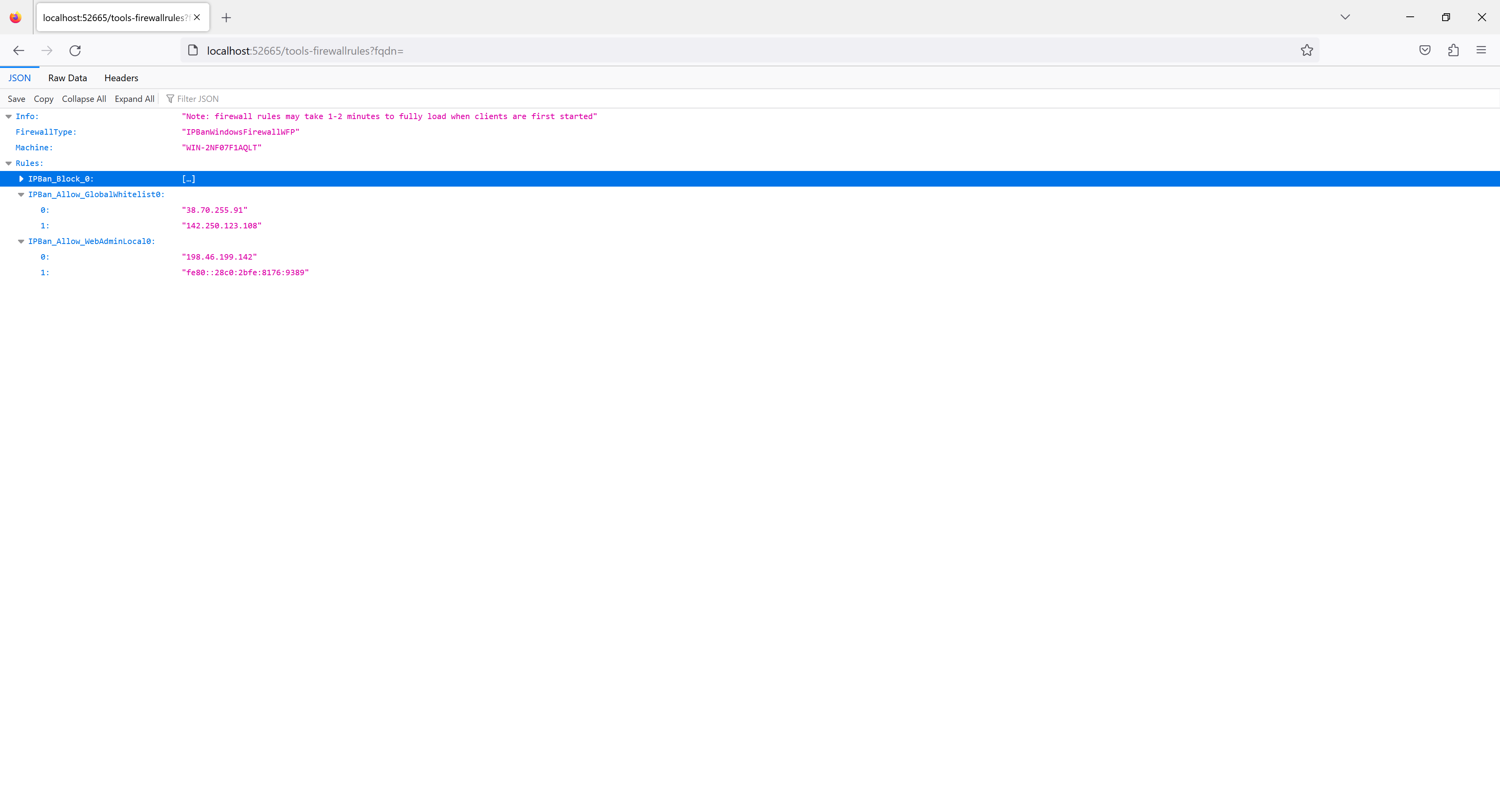
3. As of version 2.3.0, in the tools menu there is an option to grab firewall rules. This will query a random client and grab the rules. You can change the fqdn on the query string to a new client.